After using Slack for about a week or so, I was suddenly greeted by a corporate IT policy that blocked the domain…
Bored of not having it I found a way this morning to selectively send my slack.com traffic through an SSH tunnel, leaving all other traffic to flow through it’s normal routes on VPN. I’m using my dreamhost account as the SSH host, and their instructions cover most the setup.
- http://wiki.dreamhost.com/SSH_Tunneling
- Get plink http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html or other ssh software like Git Bash (it’s awesome!)
- Use a Proxy-Auto-Config (PAC) file: https://en.wikipedia.org/wiki/Proxy_auto-config#The_PAC_file
- Slack free!
SSH Tunnel
Using your ssh ( I find command-line to be the easiest via either plink or a shell emulator), you’ll connect to your ssh host and open up the tunnel. I chose 8080 as the port.
ssh -2 -D 8080 [username]@[your ssh host]
Proxy Config
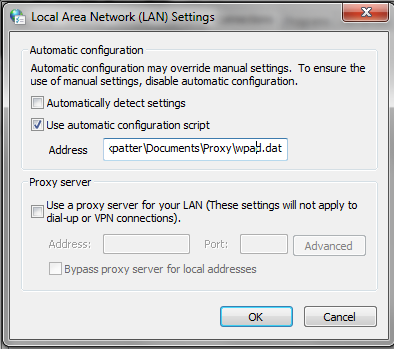
It looked like the easiest way to filter only specific traffic was a Proxy Auto-Config. I’m using Chrome on windows so I can just mess with the standard LAN settings in Chrome Settings > Proxy Settings > Advanced > Change Proxy Settings > LAN Settings. By policy I already had a wpad.dat automatic configuration script selected:
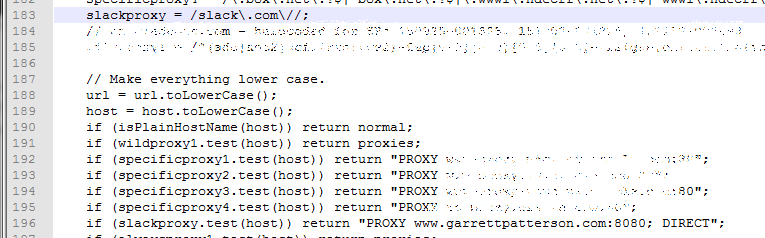
I downloaded it locally and went to edit it. Mine already had conventions in place of a bunch of matching patterns and then instructions for each match.
slackproxy = /slack.com//; if (slackproxy.test(host)) return "PROXY www.[yourproxydomain].com:8080; DIRECT";
File with edits:
Then, I re-pointed the auto-configuration script to my new local copy.
Now I’m back in!